Recently, one of my users complaining because they he could not activate Visual Studio with his MSDN account. It works fine on another machine, but not his. I tried mine, and I still got the same error - thus it was safe to rule out it is not license / user issues, but more towards computer issue.
Error :
Microsoft Visual Studio
We could not add the account
Service returned error. Check InnerException for more details
Troubleshooting :
- Back to basic - let's start from beginning... Trying to sign in will throw this error window.
- Selecting Close on above window would throw this Security Alert warning.
- Selecting View Certificate on above window would give us this.
- Let's view Certification Path, and view Root CA certificate by selecting the root certificate in Certification path | View Certificate
- So it seems the Root CA (in my case) is issued by Baltimore CyberTrust Root.
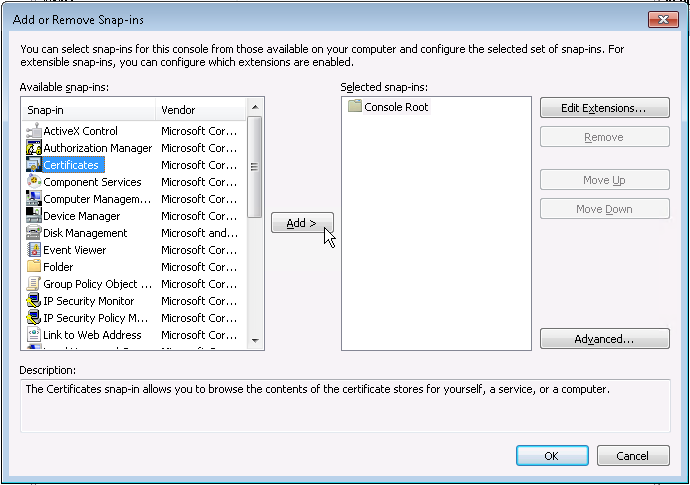
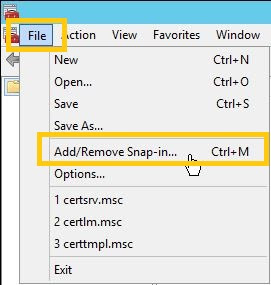
- Do I have that on that machine? Let see... Launch Microsoft Management Console by going to Run | type MMC | press Enter. Select File | Add/Remove Snap-in...
- Choose Certificate | Add >
- Select Computer account | Next >
- Select Local computer | Finish
- Select OK
- Browse to Console Root | Certificate | Trusted Root Certification Authorities | Certificates. On right column..... oh no! Baltimore CyberTrust Root certificate was not there!
Resolution :
- Now let's install the cert! download the CA (in my case, I downloaded from here : https://www.telesec.de/en/serverpass-en/support/download-area/category/72-baltimore-cybertrust-root ).
- At the same MMC console, right click at Certificate | All Tasks | select Import...
- Select Next >
- Browse to the CA file | select Next >
- Place the cert on below store | select Next >Store : Trusted Root Certification Authorities
- Select Finish
- Select OK
- Refresh the console, then we could see the cert is now installed.
- Tried to sign in again, we shall now pass!